- Test and Validate on every PR
- Build Docker Images with Github Releases
- Build ECR Images with Github Releases
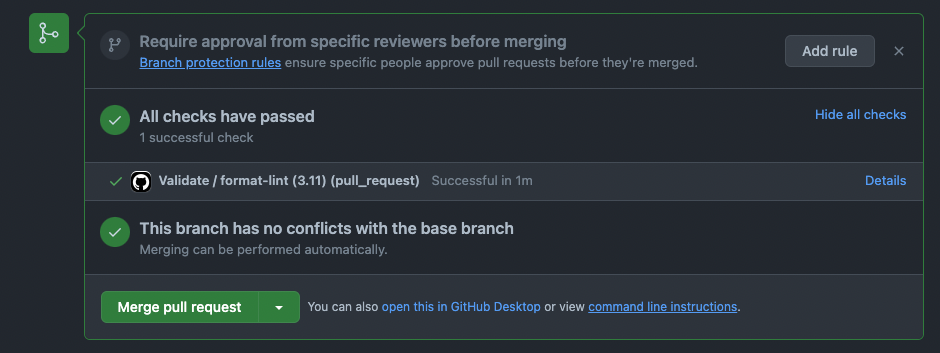
Test and Validate on every PR
Whenever a PR is opened against themain branch, a validate script runs that ensures
- The changes are formatted using ruff
- All unit-tests pass
- The changes don’t have any typing or linting errors.
.github/workflows/validate.yml file for more information.
Build Docker Images with Github Releases
If you’re using Dockerhub for images, you can buld and push the images throug a Github Release. This action is defined in the.github/workflows/docker-images.yml file.
- Create a Docker Access Token for Github Actions
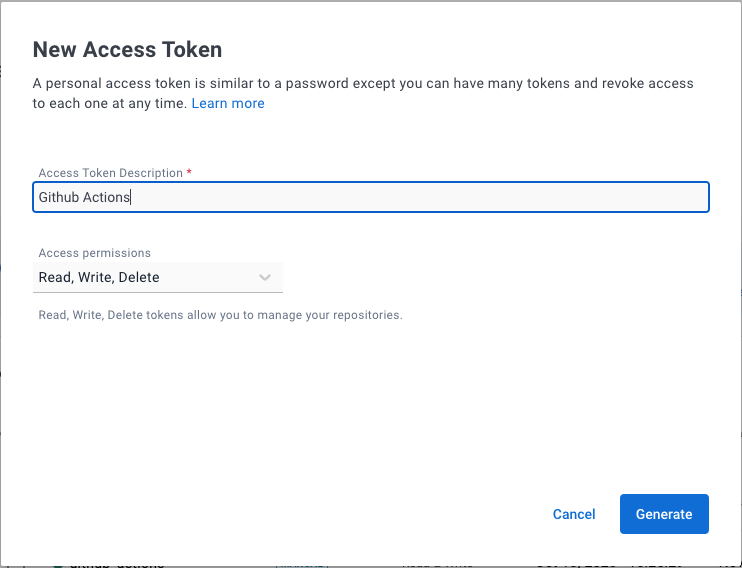
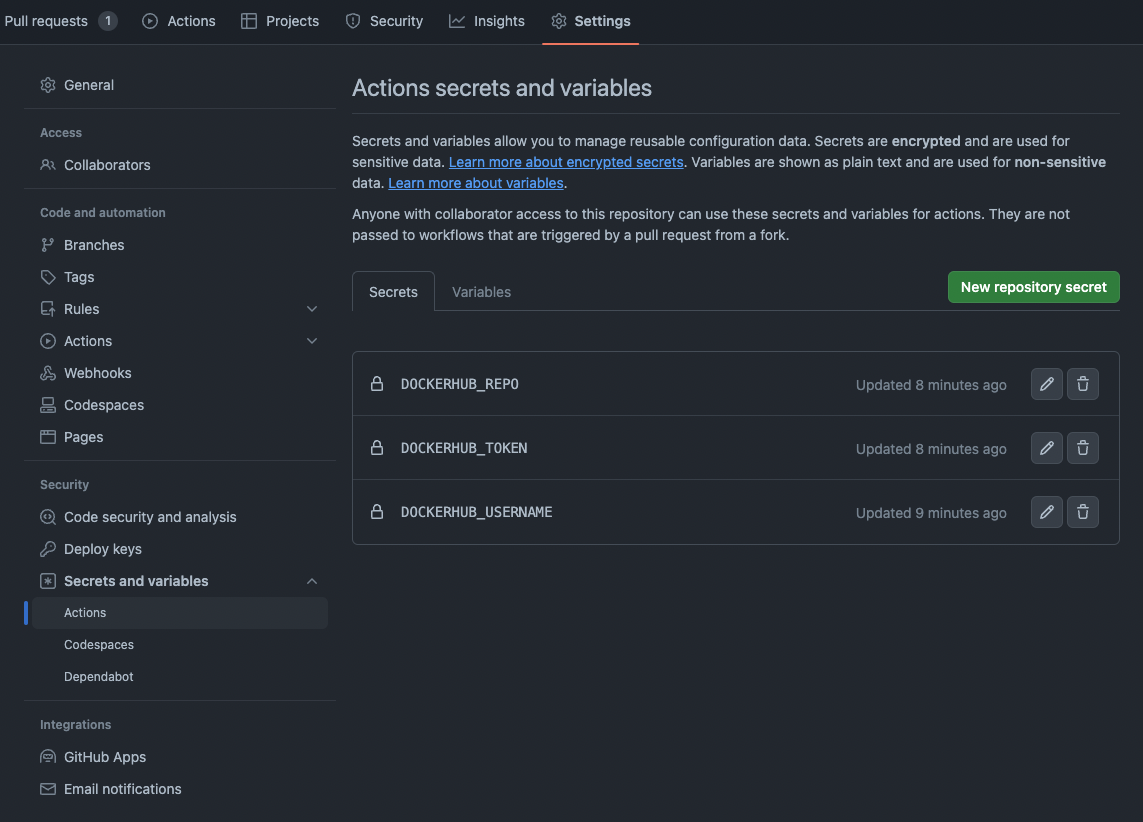
- Create secret variables
DOCKERHUB_REPO,DOCKERHUB_TOKENandDOCKERHUB_USERNAMEin your github repo. These variables are used by the action in.github/workflows/docker-images.yml
- Run workflow using a Github Release
Confirm the image name in the
.github/workflows/docker-images.yml file before running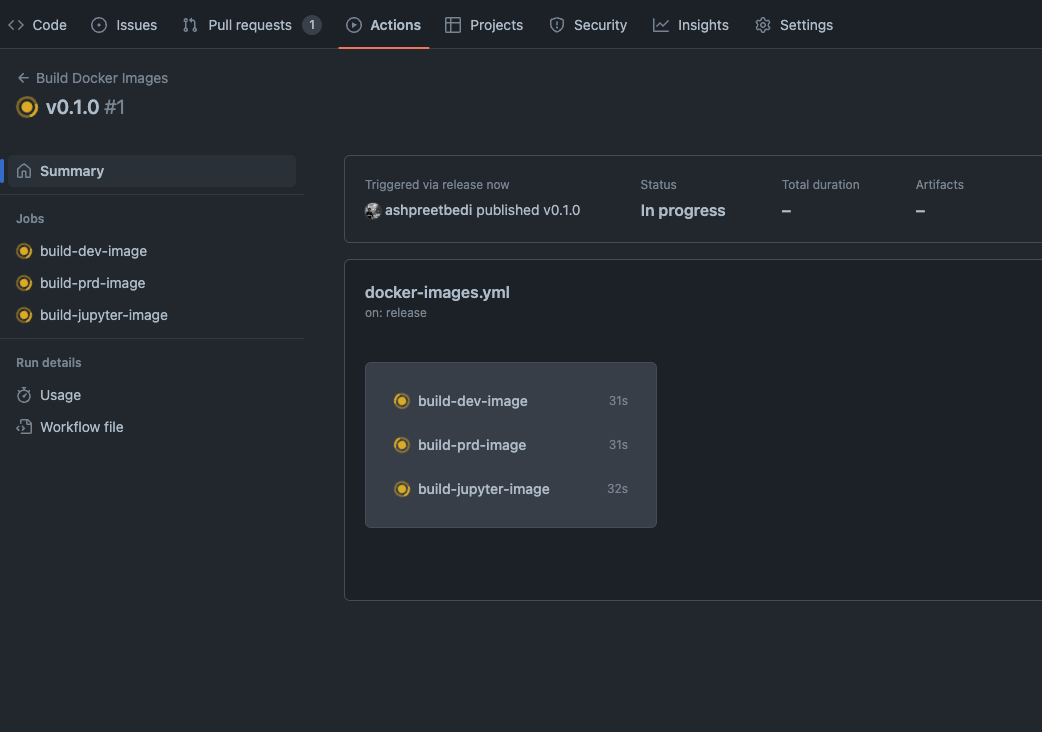
You can also run the workflow using
gh workflow runBuild ECR Images with Github Releases
If you’re using ECR for images, you can buld and push the images through a Github Release. This action is defined in the.github/workflows/ecr-images.yml file and uses the new OpenID Connect (OIDC) approach to request the access token, without using IAM access keys.
We will follow this guide to create an IAM role which will be used by the github action.
- Open the IAM console.
- In the left navigation menu, choose Identity providers.
- In the Identity providers pane, choose Add provider.
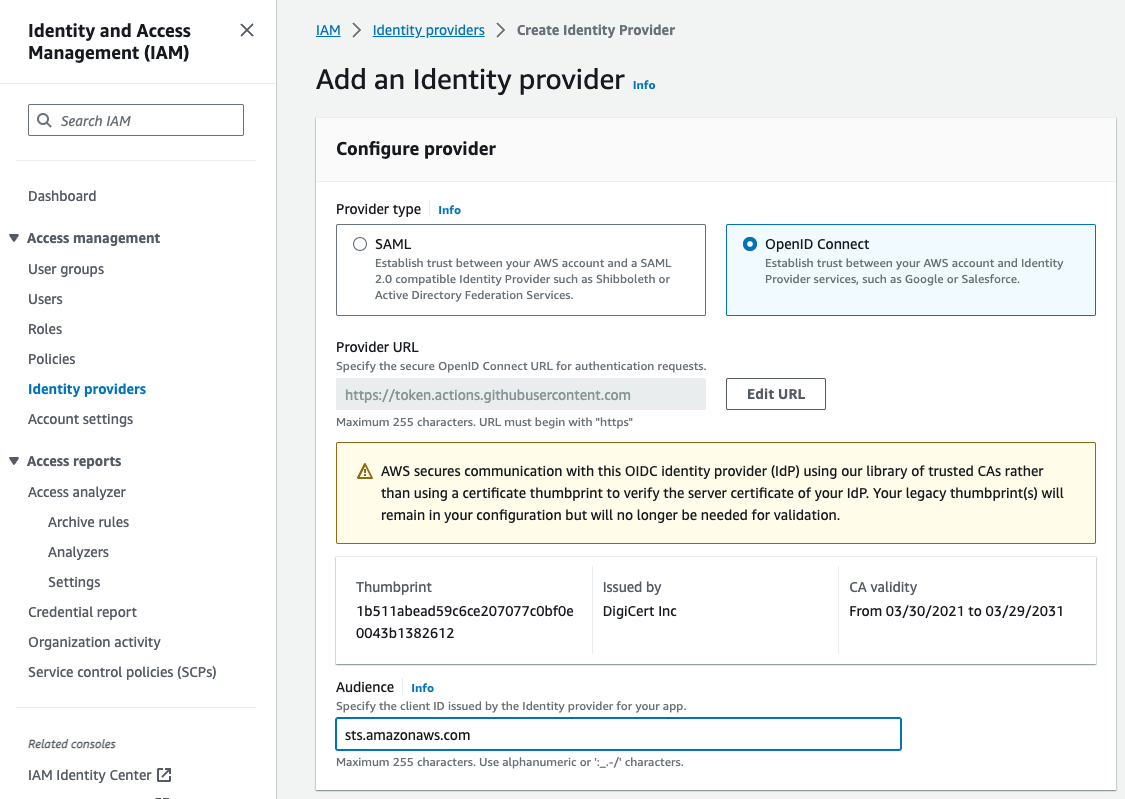
- For Provider type, choose OpenID Connect.
- For Provider URL, enter the URL of the GitHub OIDC IdP: https://token.actions.githubusercontent.com
- Get thumbprint to verify the server certificate
- For Audience, enter sts.amazonaws.com.
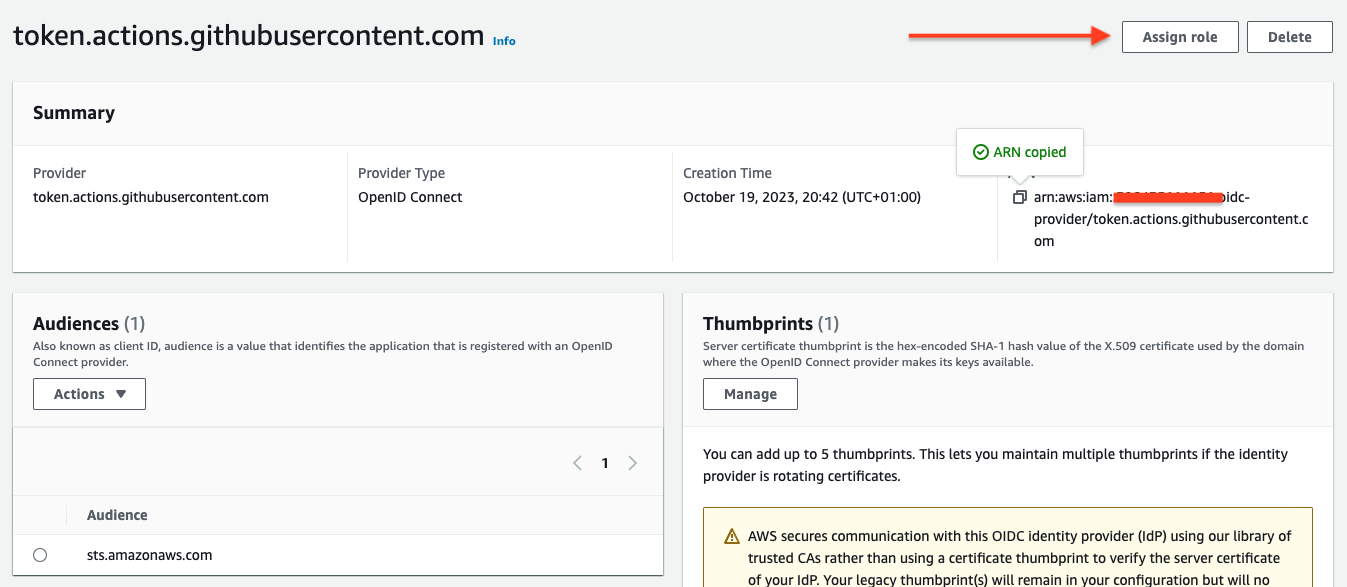
- Assign a Role to the provider.
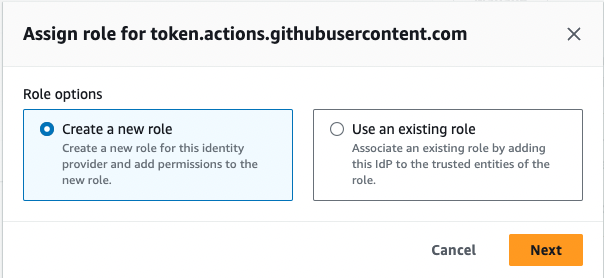
- Create a new role.
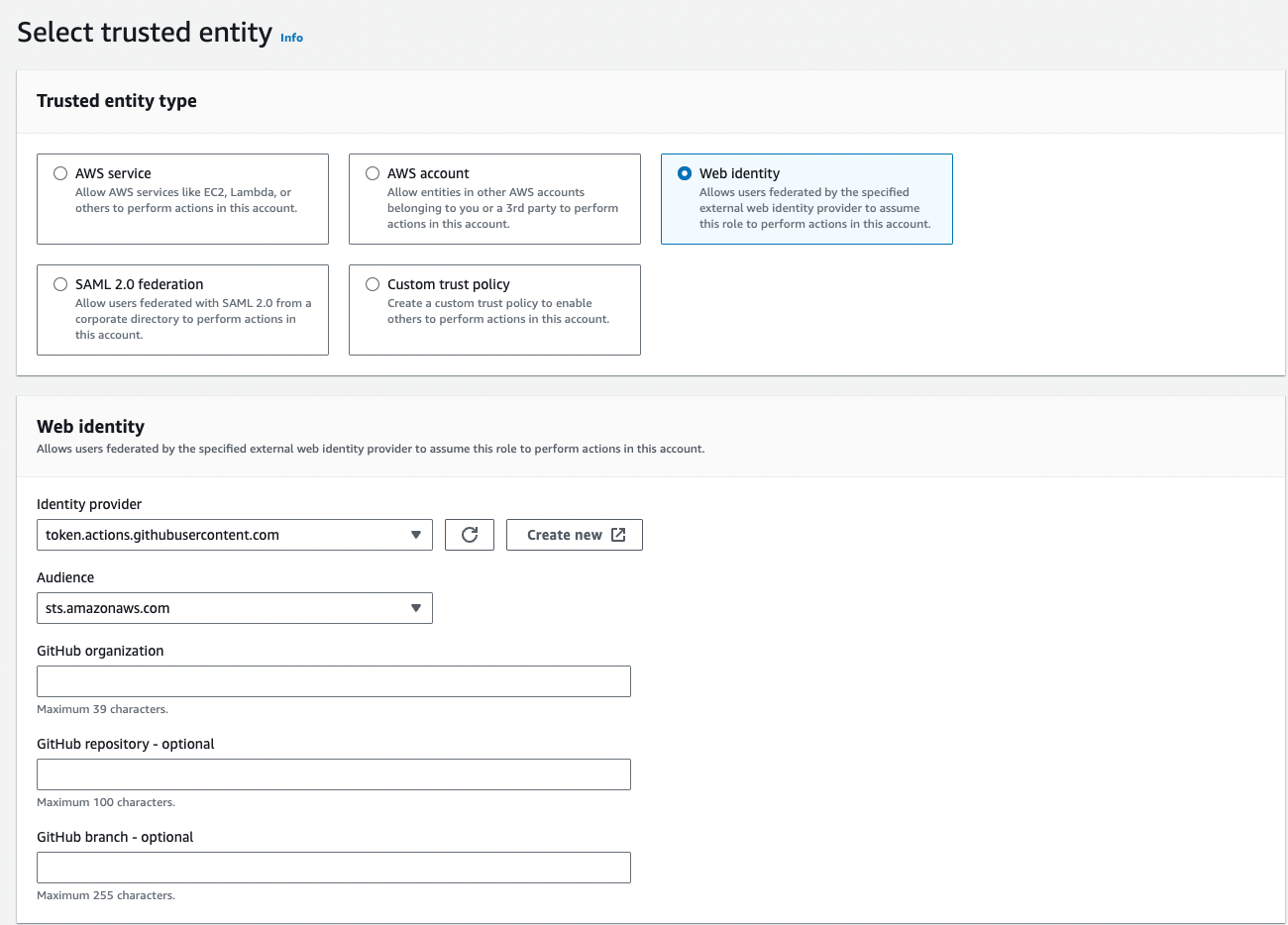
- Confirm that Web identity is already selected as the trusted entity and the Identity provider field is populated with the IdP. In the Audience list, select sts.amazonaws.com, and then select Next.
-
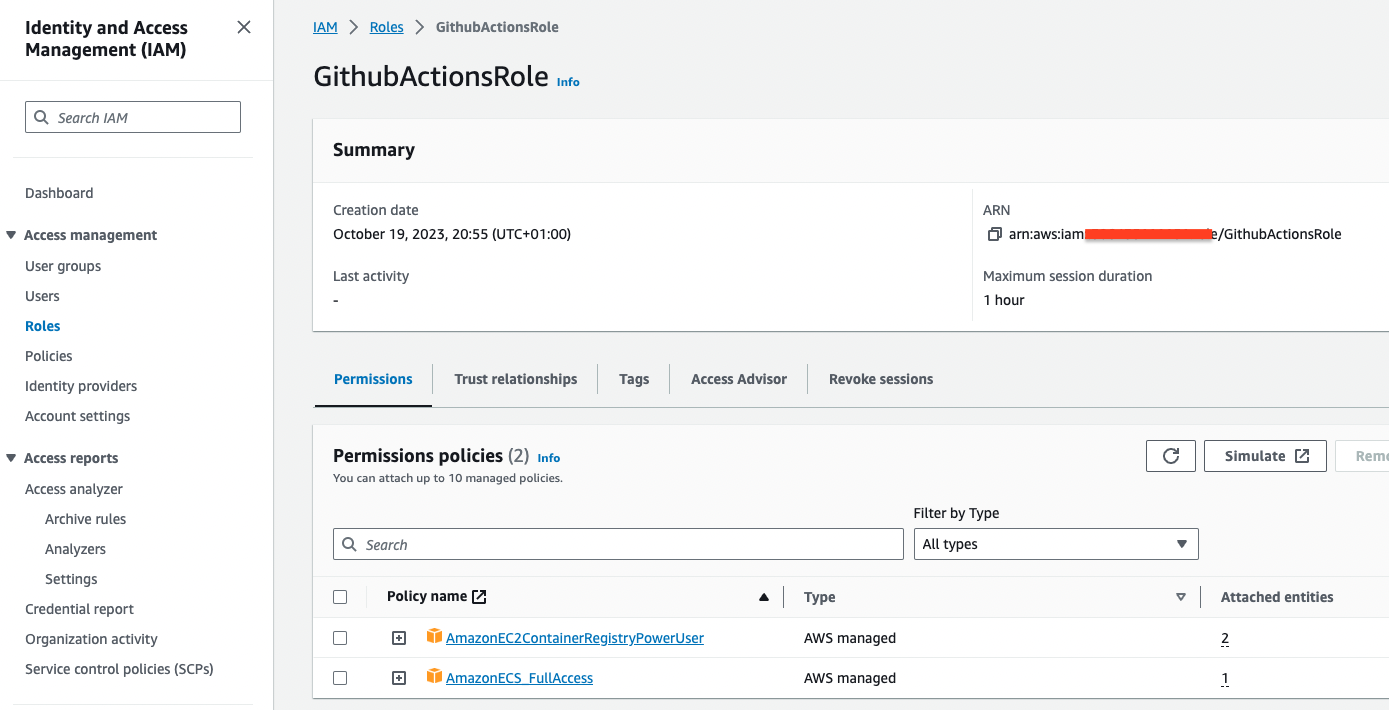
Add the
AmazonEC2ContainerRegistryPowerUserpermission to this role. -
Create the role with the name
GithubActionsRole. -
Find the role
GithubActionsRoleand copy the ARN.
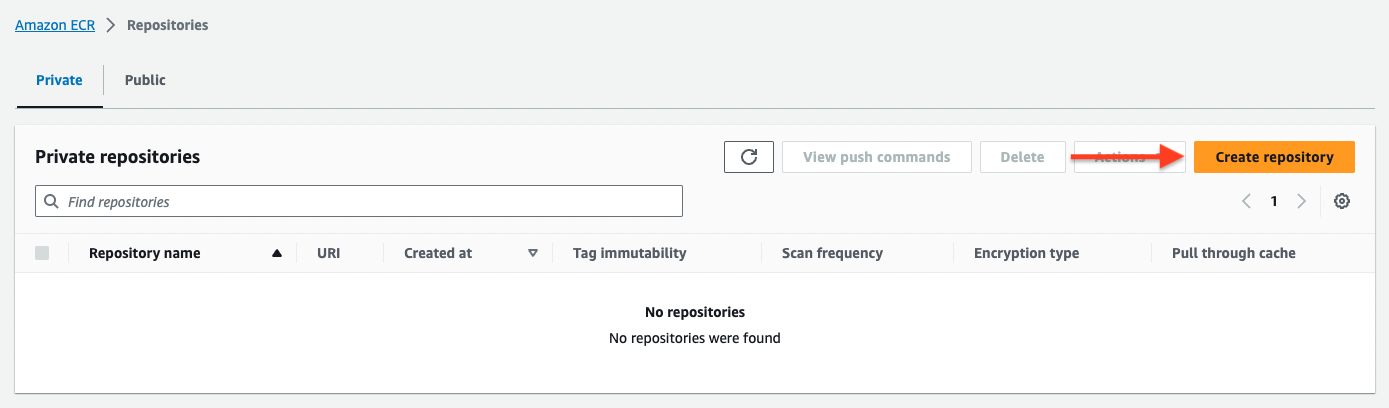
- Create the ECR Repositories:
llmandjupyter-llmwhich are built by the workflow.
- Update the workflow with the
GithubActionsRoleARN and ECR Repository.
.github/workflows/ecr-images.yml
- Update the
docker-imagesworkflow to NOT run on a release
.github/workflows/docker-images.yml
- Run workflow using a Github Release
You can also run the workflow using
gh workflow run